In the ever-evolving world of cybersecurity, staying ahead of threats is paramount for businesses of all sizes. The Australian Cyber Security Centre (ACSC) has developed a strategy known as the “Essential Eight” to assist organisations in establishing a robust cybersecurity posture.
This blog post will delve into each of these critical strategies, explaining their importance and how they can be effectively implemented in your IT environment.
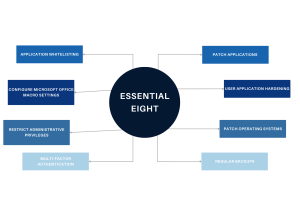
1. Application Whitelisting:
Application whitelisting is a security practice that allows only approved software to run on your systems. This approach is crucial in preventing unauthorised or malicious software from executing. Implementing application whitelisting can be challenging but is vital for protecting against various cyber threats.
2. Patch Applications:
Regularly updating applications is critical. Patches often contain fixes for security vulnerabilities that have been discovered since the last version of the software. Delaying these updates leaves your systems vulnerable to attacks that exploit these weaknesses.
3. Configure Microsoft Office Macro Settings:
Microsoft Office macros can be a potent tool for attackers. By configuring macro settings to prevent macros from executing in Office files from the internet, you significantly reduce the risk of malicious code execution.
4. User Application Hardening:
This involves configuring web browsers and PDF viewers to reduce the attack surface. Disabling unneeded features in these applications can prevent various web-based and file-based attacks.
5. Restrict Administrative Privileges:
Administrators have powerful access rights, and their accounts are high-value targets for attackers. By limiting these privileges and regularly reviewing them, you can reduce the risk of a security breach.
6. Patch Operating Systems:
Similar to application patching, keeping your operating system up-to-date is crucial for closing security gaps. Timely OS patching is a cornerstone of a secure IT environment.
7. Multi-Factor Authentication (MFA):
MFA adds an additional layer of security by requiring two or more verification methods to gain access to resources. This significantly reduces the risk of unauthorised access, even if a password is compromised.
8. Daily Backups:
Regular backups of important data, software, and configuration settings, stored disconnected from your network, can be lifesavers in the event of a cyber incident. It ensures that you can recover quickly and efficiently, minimising downtime and data loss.
Implementing the Essential Eight is a proactive step towards strengthening your organisation’s cyber defence. At ThreatReady, we specialise in guiding businesses through the complexities of cybersecurity. Our expertise in vulnerability scanning, workstation management, backup, and cyber protection ensures that your compliance with the Essential Eight is seamless and effective.
For a free detailed assessment and assistance in implementing these strategies, contact us today.